The GDPR, or General Data Privacy Regulation, is coming into force already in May this year. The regulation requires businesses to protect the personal data and privacy of EU residents. And non-compliance could cost companies dearly. GDPR pertains to the full data life cycle, including the gathering, storage, usage, and retention of data. GDPR applies to both automated and manual data processing. For companies in order to become GDPR compliant it is important to understand what is personal data.
What is personal data
Personal data is any information that relates to an identified or identifiable living individual. When collected together, different pieces of information can lead to the identification of a particular person. These pieces of information constitute personal data. For example, a person’s full name is an obvious identifier. But a person can also be identifiable from other information, including a combination of identification elements such as physical characteristics, pseudonyms, occupation, address etc. Personal data that has been de-identified, encrypted or pseudonymized but can still be used to re-identify a person remains personal data.
However, personal data that has been rendered anonymous in such a way that the individual is no longer identifiable is not considered personal data. For data to be truly anonymized, the anonymization must be irreversible.
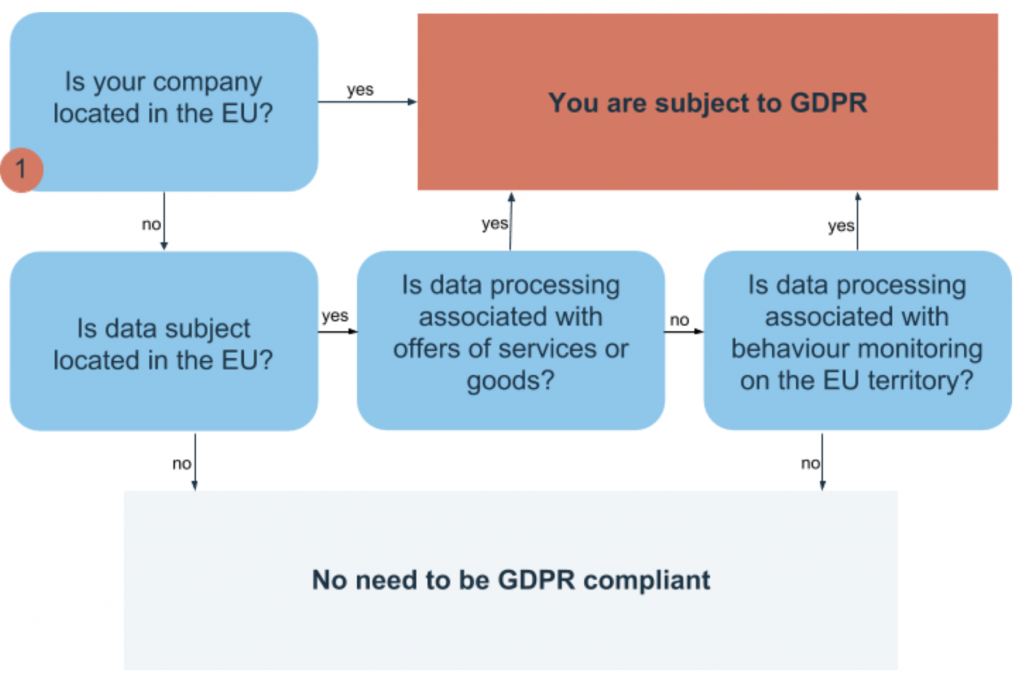
GDPR geography
What’s new. How is GDPR different from the EU personal data protection law
Pseudonymization. It is necessary to keep the info that allows to identify the person and the data about this person separately. For example, person’s name should be kept separately from the history of his actions in the app. This way, in case of the data breach it won’t be possible to match actions and an individual.
New rights for data subjects. For example, the right “to be forgotten”. All the personal data about an individual has to be deleted upon request. Or the right “to be portable”, means that you should be able to transfer your personal data from one service provider to another in case you decide to switch.
Data breaches. It will be necessary to inform the authorities and users about any data breaches within 72 hours after they are found.
Data Protection Officers. Every large company will have to hire a Data Protection Officer (DPO).
Privacy by default and privacy by design (will be discussed further).
The steps you need to undertake to get closer to GDPR compliance
Step 1. Make “private” the default setting.
Starting to work with any software, the user should have settings with maximum privacy. In case the user does not make any changes in the settings, the protection level should remain unchanged. The application should not require any actions from users to obtain maximum level of personal data protection.
Step 2. Embed privacy.
Introduce privacy into your software from the very beginning, even before the first piece of personal information gets into the system. Privacy should be at the core of any software and not be installed with some plugin. Lack of privacy cannot be the price for apps functionality, meaning you can’t present your users with a challenge – privacy or functionality. Such software will be illegal when GDPR becomes effective.
Step 3. Identify personal data and the processes that use it.
Set up and maintain a personal data register. It can be a separate document or part of the Information Asset Register. Use this tool to keep records of personal data you collect, indicating places where it is stored, responsible file owner, access level, storage period, data accessibility etc. Determine in advance who in your company maintains this registry.
You can use any familiar tool to keep track of personal data you process, for example, Data Flow Charts, Processing Registers, Data Inventories, Data Indexes, Data Mappings.
Step 4. Minimize personal data.
Use of personal data must be reduced to the minimum sufficient level to achieve the goal of processing. Minimize user identification wherever it is possible. Embed the function of deleting unnecessary and used data.
This step will not only protect the privacy of users, it will save you from a headache in case of a hacker attack on the app. You won’t have to notify the authorities and subjects of personal data about the data breach or pay a huge penalty for negligent attitude to the rule of data minimization.
Step 5. Record the implementation of GDPR rules.
Companies are obliged not only to follow GDPR regulations but also be able to documentary prove that they are GDPR compliant. Even if the company followed all the regulations, but forgot to document it, all the undocumented measures will be considered unimplemented. The audit will show that nothing has been done in the company to become GDPR compliant. That is why companies need to hire DPOs, whose duty will be to document all the undertaken measures towards GDPR compliance.
Step 6. Obtain informed consent for the processing of personal data.
In order to process the data, it will be necessary to obtain consent from users in advance. The consent should indicate, how the information will be processed, who and how will transmit it to another country. The text must be unambiguous and understandable. You are required to provide comprehensive information on the processing of the user’s personal data: what data, when, by whom, where, what for? Moreover, silence or inactivity does not mean that the user agrees, for example, the users will have to voluntarily tick the “receive newsletters” item themselves.
Step 7. Implement information security measures.
The regulation has increased penalty charges for information leakage. From now on companies will not only pay for hacker attacks with their reputation but will be subject to serious fines. In other words, companies will have to pay for inadequate care for the privacy, integrity, and accessibility of users’ personal data. Therefore, it is necessary to take care of the protection system during the initial stage of software development. The authors of GDPR refer to encrypting as one of the measures, but software creators are free to choose any protection measures they find relevant.
Although GDPR does not refer to particular information security standards, ISO 27xxx certification is one of the measures that will allow to show the regulatory authorities that you have a solid data security system in place.
Under the shadow of GDPR, it is easy to understand why companies are concerned about the regulation with the potential to have such a profound impact on their business. The GDPR represents a huge shift in the way businesses will be expected to handle data. However, compliance with GDPR will soon become a point of differentiation, and the sooner businesses are GDPR compliant, the sooner they will begin to reap the rewards of standing out from the competition. Enhanced customer loyalty and confidence that their personal information is in good hands and maximized selling opportunities are just one of many other benefits the companies will be getting.


